Penetration Tester Management with Built-in Quality Assurance
Assist Penetration Tester during penetration test engagement
with intuitive test case suggestion and Igider Core Lead review

All-in-one Solution for
Enhancing Application Security
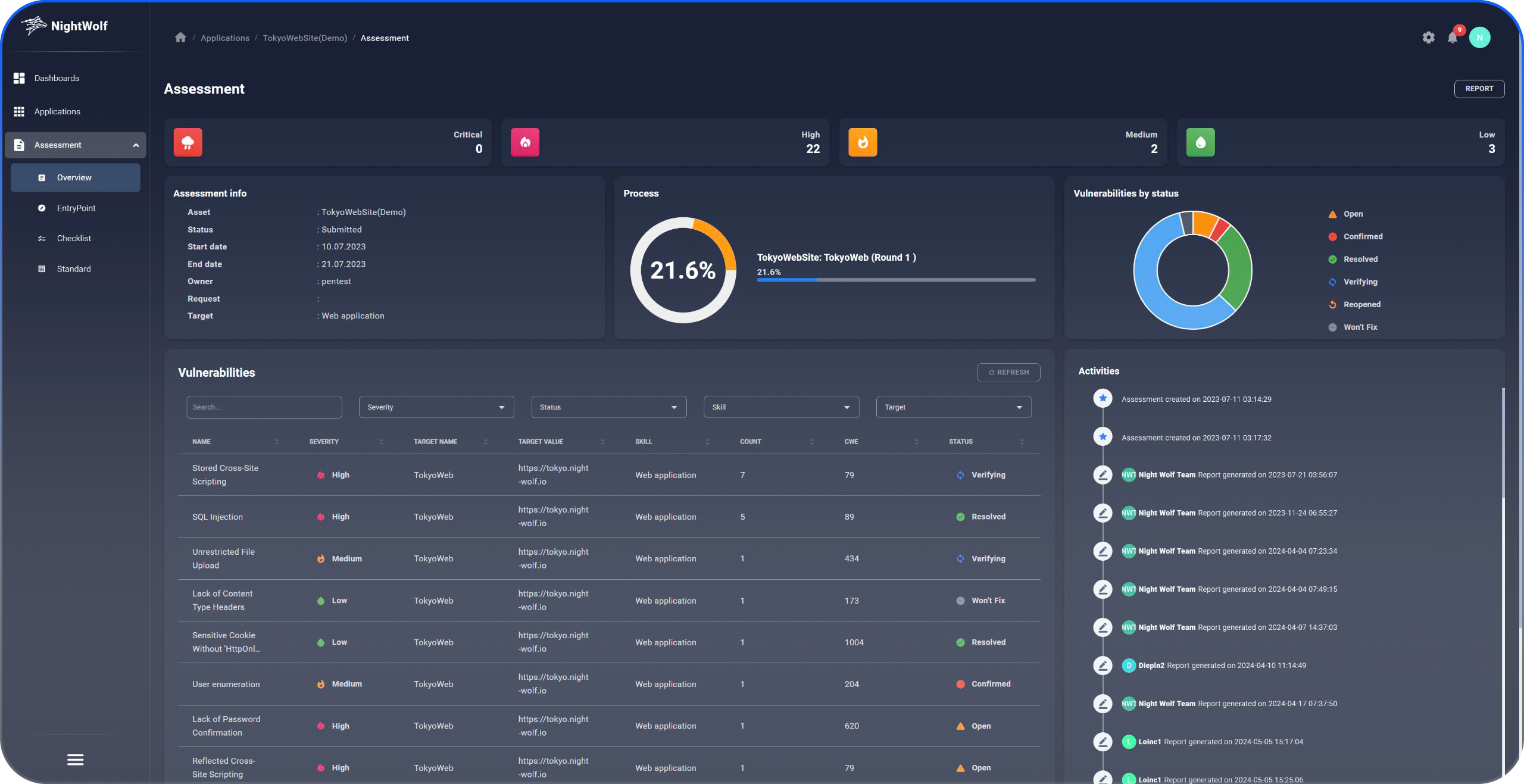
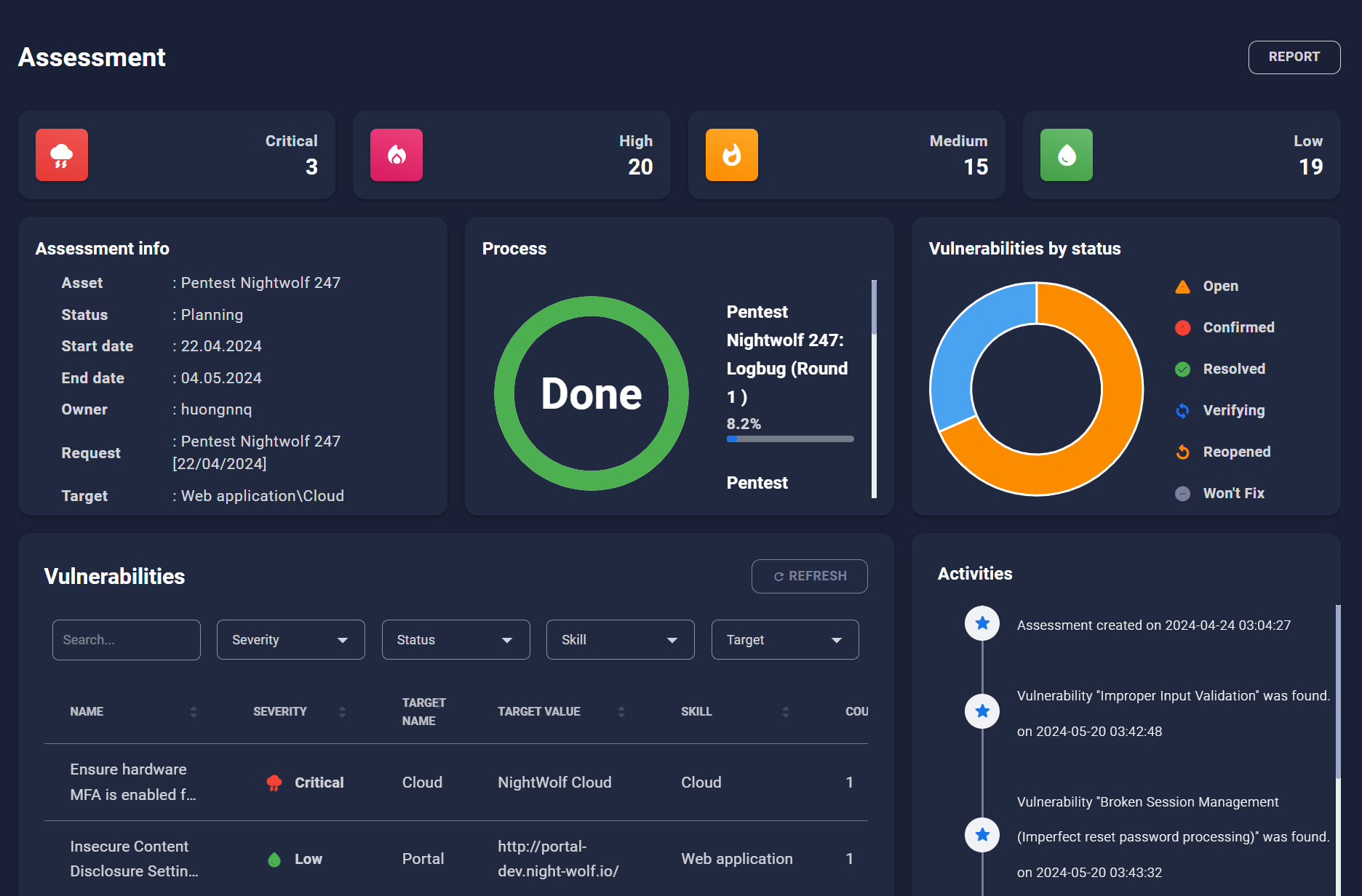
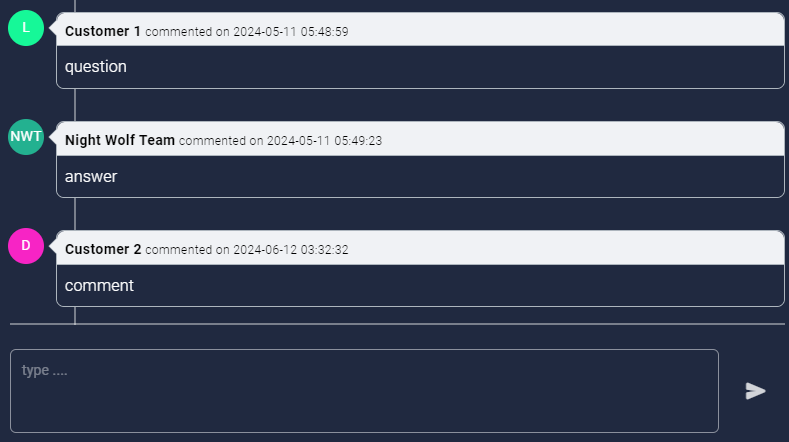
Obtain clear and concise information about the asset, track the test’s progress through secure communication and share files.
On-demand distribution of report